Metro and Carrier Ethernet
Ethernet is playing an increasingly important role in connecting sites. Both in local area networks (Metropolitan Area Networks/MAN) and in wide area networks (WAN). Ethernet is located on Layer 2 of the OSI network model. This is one layer below the Internet Protocol, which is on Layer 3.
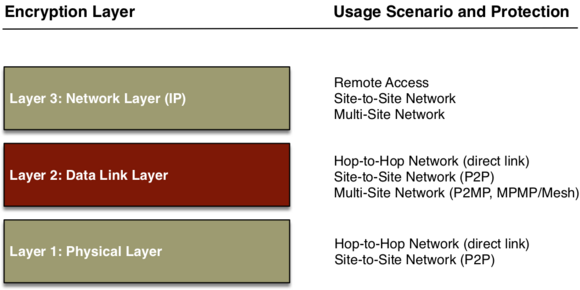
Network encryption provides the greatest efficiency and security when it is done either natively at or below the layer being used. Encryption below the layer in use may sacrifice flexibility.
The rapidly increasing demand for dedicated Layer 2 encryptors has a simple reason: security and efficiency coupled with cost savings. More than 99 percent of attacks on networks occur at Layer 3 through 7, and Layer 2 encryption of inter-site traffic - when using authenticated encryption - grants full protection for the network, including confidentiality, intrusion detection, intrusion prevention and firewall. That's why there are more and more customers for such solutions, including those with over 900 Layer 2 encryptors in 24/7/365 use.
Different Approaches
There are different approaches and techniques for network encryption. These have a direct impact on the supported application scenarios and on security.
There are also different ways of encrypting Ethernet. This can be done at layer 1, at layer 2, as well as at layer 3 or higher. It is most efficient on layer 1 and on layer 2, and most flexible on layer 2 and layer 3. The optimum combination of efficiency and flexibility is offered by encryption on layer 2. But there are differences there, too.
Hop-by-hop vs. end-to-end
End-to-end encryption is preferred for connecting sites. Hop-by-hop encryption only works in a limited number of scenarios.
With hop-by-hop encryption, data is decrypted at each hop, processed in unencrypted form, and then sent on to the next hop, again encrypted. The situation is different with end-to-end encryption, where the data remains secured throughout the transmission between sender and destination.
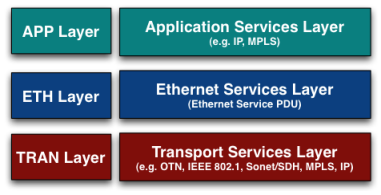
The three-layer model shows the environment in which an encrypter should be able to do its work. IEEE 802.1 (Ethernet) is only one of many possible transport options, and the network protocols from the Application Services Layer can in turn also serve as the transport layer. Fully supporting and securing Carrier Ethernet-based networks is complex.
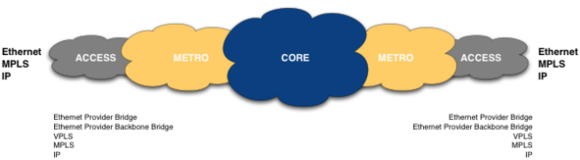
Each of the metro and Carrier Ethernet topologies requires a transport network that meets their respective requirements. Native Ethernet transport networks are found primarily in the access and metro areas, but a different transport network is often used even there. OTN, MPLS, IP and in some cases Sonet/SDH are common. The term "Carrier Ethernet" covers every transport network used for the transport of Ethernet frames. The transport networks used within a MAN or WAN are usually not homogeneous. Depending on the placement of the encryptor and the transport network used, the original Ethernet frame is encapsulated or tunneled. However, the Ethernet frame that is delivered is identical to the Ethernet frame that was sent.
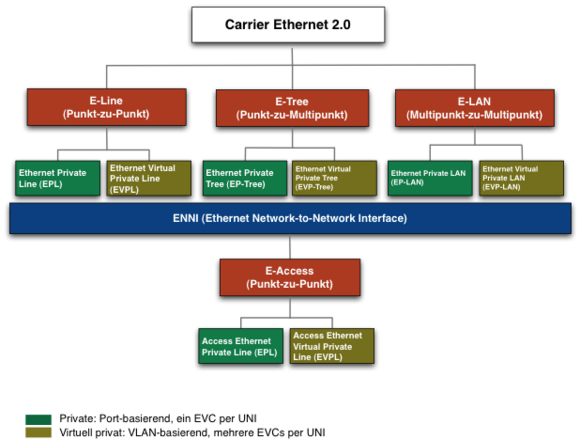
The Metro Ethernet Forum (MEF) has defined and standardized three different topologies for regional and wide area networks. The original scenario was limited to a single telecom provider offering all access and network services to the customer. This proved to be impractical, especially for wide-area networks. Therefore, a standardized interface between the Ethernet services of different telecom providers was defined. The Ethernet Network-to-Network Interface (ENNI) standardizes interconnectivity between carrier Ethernet networks.
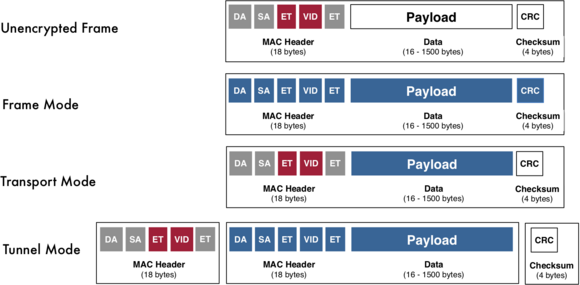
Encryption Modes
The particular encryption mode determines which parts of an Ethernet frame can be encrypted. In frame mode the entire Ethernet frame is encrypted, in transport mode it is the Ethernet payload that is encrypted and in tunnel mode it is the entire Ethernet original frame that is encrypted. Each mode has its advantages and disadvantages. The advantages are in protection (frame mode, tunnel mode), the disadvantages are in flexibility (frame mode), protection granted (transport mode) and overhead (tunnel mode). In the end, it is a trade-off between network costs and protection needs. Transport mode is used for the most part, tunnel mode in some cases, and frame mode in other cases. At layer 2, the IP packets being transported can be completely encrypted without the need for a tunnel mode. The IP packet is the payload of the Ethernet frame and can be encrypted in its entirety in transport mode. Authentication and integrity protection refer to the Ethernet frame with the encrypted IP packet as payload.
Detailed information can be found in the introduction to layer 2 encryption