Different topologies, different key systems
Depending on how many participants a network consists of and how the communication flow should be designed, different topologies and key systems come into question.
There are three basic types:
- Point-to-point (P2P)
- Point-to-multipoint (P2MP)
- Multipoint-to-multipoint (mesh)
Key Systems
Pairwise keys and group keys
There are different approaches to structuring key allocation and key usage: as a pair, where a different key is used between two parties for each direction, and as a group, where the same key is used within a group.
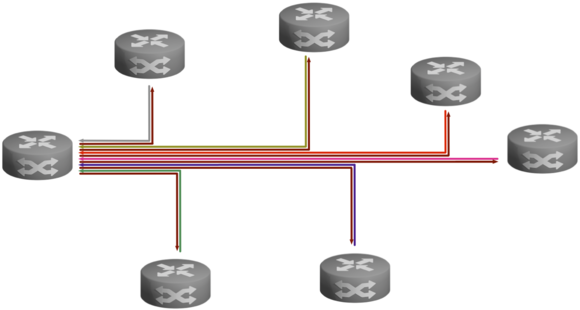
Point-to-Point
For point-to-point connections it then looks like this:
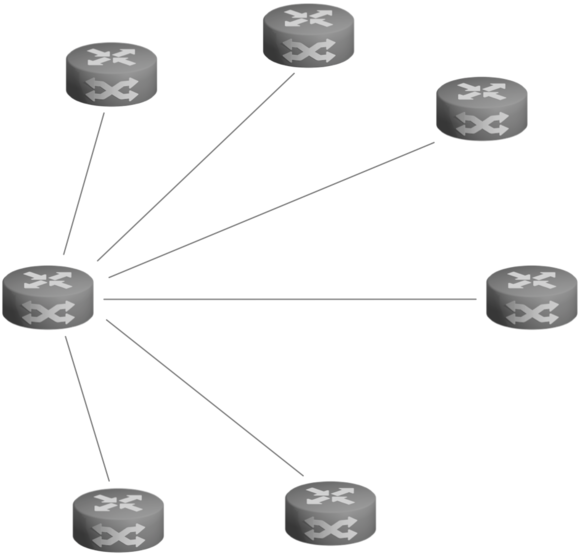
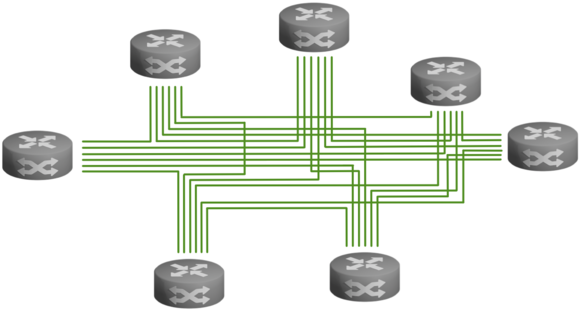
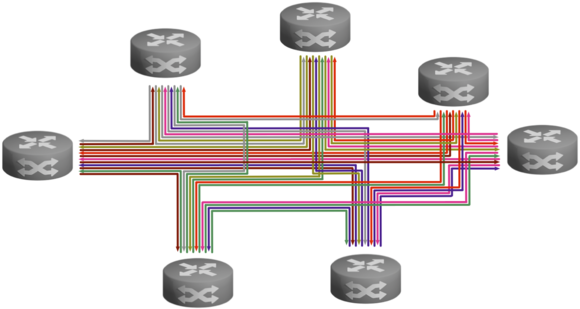
Point-to-Multipoint (P2MP)
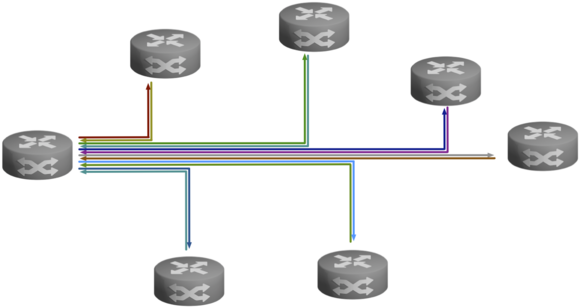
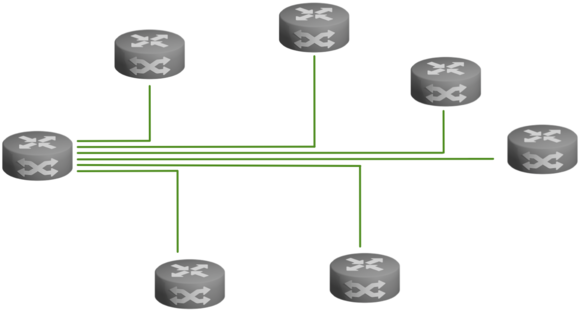
For point-to-multipoint topologies, you can use either a pairwise key system or a group key system. A bidirectional group key system considers the entire network as a single group. Each site is part of that group and everyone in that group uses the same key. An undirectional group key system restricts group membership to a site's outgoing connections. All of a site's outgoing connections together form a group and use the same group key. Since each site has outgoing connections, there are multiple groups.
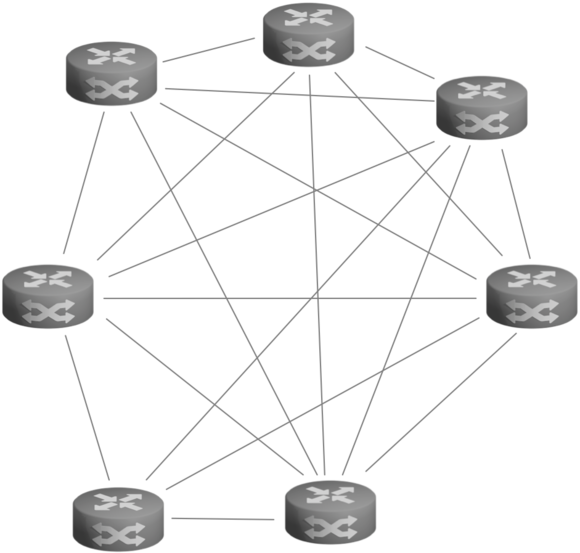
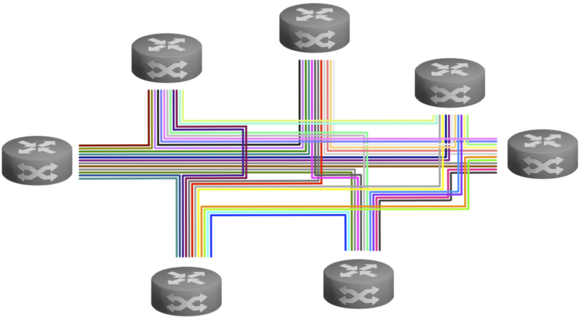
Multipoint-to-Multipoint (MP2MP/Mesh)
In multipoint-to-multipoint topologies, each site can communicate directly with the other sites and do so simultaneously. Group key systems are best suited for this, as they can encrypt the simultaneous flow of data to one site as well as to multiple sites, which also gives operational advantages, especially with multicast. With paired keys, multicast must also be encrypted individually for each connection.