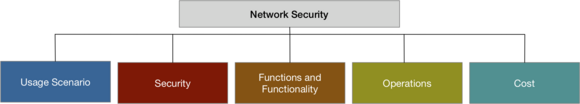
Network encryption
Various factors play a role in selecting the appropriate network encryption solution. The focus here is on static networks between two or more sites, and in particular on dedicated network encryption solutions. These solutions, if well implemented, can also provide firewall and denial-of-service protection functions at the native network layer.
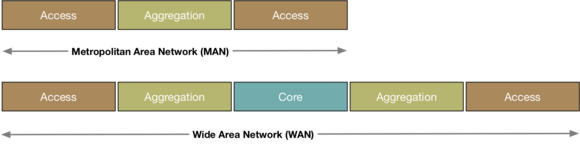
MAN and WAN
Unlike local, internal networks, metropolitan area networks (MAN) and wide area networks (WAN) aggregate the data flow of several different customers for transport. Both are networks that run over public land and are therefore subject to different threats than internal networks. One example can be found in denial-of-service attacks that come from the outside, flooding the network access with data and thus overloading and crippling the network access. The big difference between MAN and WAN is the distance. This means that network traffic travels longer and further. This increases both the latency and the potential for danger.
What can be encrypted and how is it done?
State-of-the-art encryption requires prior authentication and authorization of the remote station (zero trust) as well as encryption (confidentiality), authentication (confirmation of origin) and integrity protection of the data to be transmitted. Depending on the network and the network layer, some network information that is in the header of the frame or packet must remain unencrypted in order for the frame or packet to be switched or routed.
The following basic principles apply:
- as much of the transmitted frame or packet as possible should be encrypted, authenticated, and integrity protected
- what cannot be encrypted should be authenticated and integrity protected as much as possible
- the deeper the network layer, the more information of the upper network layers can be encrypted
- static networks between sites can be better secured than dynamic networks that are built on demand
After successful mutual authentication and authorization, the parties can negotiate a Key Encryption Key (Master Key). This key is then used to encrypt the Data Encryption Key (Session Key). The Data Encryption Key is used to encrypt the network traffic. This key agreement and key exchange takes place on the control plane, i.e. between the devices. It therefore makes sense for static network connections on Layer 1, Layer 2 and Layer 3 to encrypt the Control Plane on the same network layer as the Data Plane.
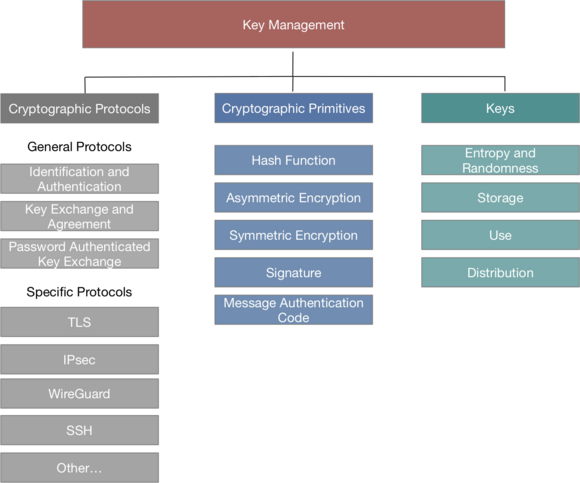
Key Management
No encryption without keys. They are not only required for the data encryption, but also for the authentication. Addiional cryptograhic primitives and funtions are rquire for the integrity protection. Key management covers all of these aspects and is one of the core aspects for network encryption. Without secure keys, even the best encryptiuon doesn't provide suffiecient security. Each encryption algorithm is dependent on the key security.
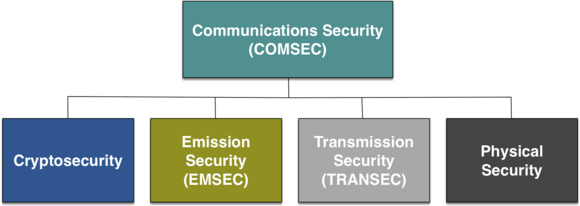
Communication Security
Communication security depends only in part on the encryption algorithms used and the randomness of the keys. If the encryption device itself is not secure, the best encryption will be of no use. Then the insecure device, where the data is exposed in plain text, becomes the point of attack. And this is more often the case than one would generally assume. Secure security devices are the exception rather than the rule. Even security certifications are of no use.
What is required is secure cryptography and a secure device. In addition, it is possible to obfuscate network traffic by means of traffic flow security (Transec) and to protect the device against electronic emissions to the outside.
Integrated or dedicated
Cheap and secure are mutually exclusive. Well and securely implemented functionality also costs money. If it's purely a matter of price and speed with low security needs and maximum functionality requirements, integrated appliances such as the combination of router, firewall and network encrypter are a cost-effective way to go. At least apparently. Because this also increases the number of attack vectors and the number of as yet unknown but exploitable security l Poor product quality then leads not only to reduced availability because of the necessary patches, but also to higher OpEx, higher security risks and the risk of reputational damage.
High security and comprehensive functionality at high processing speed can only be provided by specialized encryptors. In the case of multi-client and multi-client-capable systems, it is also possible to obtain encryption as a service without having to hand over the key sovereignty. In this way, there are no acquisition costs and only operating costs are incurred.